Tom is an enterprise’s IT manager who leads a team that is responsible for driving the company’s cloud transformation. They have started a project on AWS Landing Zone with Control Tower, with the aim to introduce the number of benefits that their cloud service partner had been talking about for quite some time. Tom and the team are conscious that there can be various approaches on many aspects. They also have questions; for example, after the Control Tower managed Landing Zone is deployed, how can they maintain the best practices, prevent architectural and operational drifts – on the ongoing basis. They are in a sector that demands greater and greater data security governance so logically they would like the peace of mind knowing that the Control Tower structure will continue to fulfil this purpose, without risking itself becoming a toolset that is too complex, for their relatively small team. Their cloud service partner suggested for them to consider Landing Zone Accelerator.
The Landing Zone Accelerator (LZA) on AWS solution focuses on landing zone solutions that align with AWS best practices and multiple global compliance frameworks. It is highly recommended for customers with highly-regulated workloads and complex compliance requirements (LZA itself does not guarantee compliance status but helps an organisation’s journey to those compliance frameworks), as well as any institutional customers that do not require high degree of customisations to their Control Tower setup. LZA helps to better manage and govern multi-account AWS environments through a streamlined, low-code, yet comprehensive solution.
Let’s revisit what a landing zone is first.
‘A landing zone is a well-architected, multi-account AWS environment that is scalable and secure. This is a starting point from which your organisation can quickly launch and deploy workloads and applications with confidence in your security and infrastructure environment. Building a landing zone involves technical and business decisions to be made across account structure, networking, security, and access management in accordance with your organisation’s growth and business goals for the future.’ – AWS documentation
So ultimately a landing zone is a foundational structure that as a starting point, can enable quality approaches on:
• Migrations to AWS
• New workload developments
• Continued iteration and extension over time
As discussed in previous blog pieces, you do not have to have Control Tower with a Landing Zone setup, though enterprise and government entities will typically see the compelling benefits of a Control Tower managed Landing Zone solution.
Landing Zone Accelerator on AWS (LZA)
LZA offers accelerated solution on the primary components of Control Tower Landing Zone environments:
• The security governance controls and
• The cloud infrastructure foundation
At the heart of the LZA is an ongoing pipeline to deploy core landing zone infrastructure, with emphasis on Automation, Data Security, Compliance and Support.
LZA is an open-source solution. Yaml based configuration files and GitHub project are inputs to the LZA which in turn will provision the feature/issue iterations to the AWS environments.
Below is a descriptive diagram by AWS on where LZA fits:
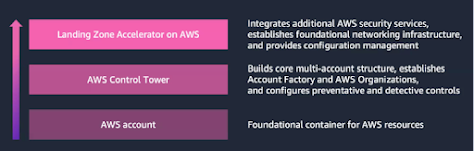
A few keywords describing LZA would be: streamlined, low-code, less-customised (comparing to CfCT)
Major solution benefits include:
• Build a secure, compliant, multi-account foundational AWS environment in days instead of months or years
• Automated implementation
• Reducing defects in code as it comes with a single managed codebase
• Prescriptive
LZA does not have to have Control Tower as it can work directly with AWS Organisations. But similar to what we mentioned earlier, Control Tower is the typical approach that LZA works on top of.
There are mandatory accounts LZA needs: Management, Audit and LogArchive (please note it is not Log Archive, e.g., no space between the two words. When the Log Archive account was provisioned by previous Control Tower implementation, renaming was needed to remove the space.)
The following additional prerequisites apply:
• AWS Code Commit, Code Build, Code Pipeline
• GitHub
Below is an example LZA enabled cloud account structure provided by AWS for the ease of concept understanding:
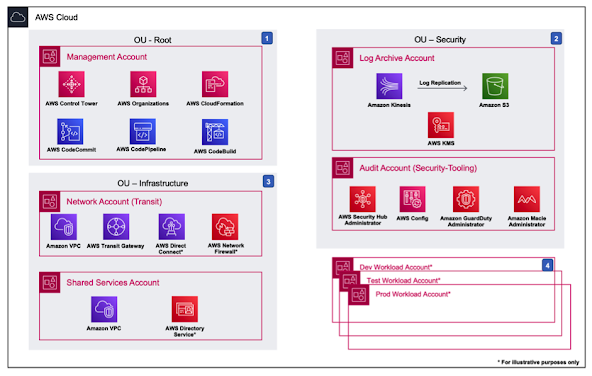
The LZA configuration files are the primary user input interaction points. They are yaml files, easy to grasp, and straightforward to edit. A total of seven configuration files apply:
• accounts-config.yaml
• global-config.yaml
• iam-config.yaml
• network-config-yaml
• organization-config.yaml
• security-config.yaml
• customizations-config.yaml (optional)
Below is a screenshot of the CodeCommit page, depicting six configuration files:
Clicking on a file name will allow viewing and editing of its lines.
A global-config.yaml file may start with looking like this:
As we can see, toggling line values from false to true, and adding additional inputs (snippets) are quite straightforward. Same goes for all other configuration files, such as network-config.yaml, where you can supply detailed network configuration inputs.
AWS has provided sample configurations for various sectors, like for education, healthcare, finance, etc, to be used as ready blueprints, based on which further specific inputs can be done.
LZA’s source code is open source, GitHub based. A CodeBuild project is utilised to run the LZA pipeline CDK project to deploy LZA. The pipeline uses AWS CodeBuild to orchestrate for each action’s completion. Here are the orchestration flow steps:
1. Source
1.1.
Source
2. Build
3. Prepare
4. Accounts
5. Bootstrap
6. Review (optional)
6.1.
Diff
7.1.
Key
8. Organization
9. Security_Audit
10. Deploy
10.1.
Network_Prepare
10.2.
Security
10.3.
Operations
10.4.1.
NetworkVpcStack
10.4.2.
NetworkVpcEndpointsStack
10.4.3. NetworkVpcDnsStack
10.5.
Security_Resources
10.6. Network_Associations
10.6.1.
NetworkAssociationsStack
10.6.2.
NetworkAssociationsGwlbStack
Sample screenshots are provided below as a visual guide:
Above is just a quick explanation on why LZA can claim to accelerate the build of a secure, compliant, multi-account foundational AWS environment from months to days, and can provide ongoing acceleration on continued iteration and extension over the years to come for an organisation.
It is to note that Landing Zone Accelerator on AWS (LZA) takes a different approach to CfCT (Customizations for AWS Control Tower). If we compare the angles that CfCT and LZA take at an ultra high level:
- CfCT is for the customisation capabilities
- LZA is for the prescriptive, streamlined approach
In real world scenarios, since a majority of the organisations may not need or desire high levels of customisation, LZA would be the path that more organisations take. Both CfCT and LZA are growing and evolving in their capabilities and reach. It will be exciting to see how they help more with the cloud transformation journeys in the coming years.
-- Simon Wang











Comments
Post a Comment